2021. 12. 16. 09:05 WorkHolic
Apache Log4j 1.2.x 버전 취약점 해결 방법
Apache Log4j 1.2.x 버전 취약점 해결 방법
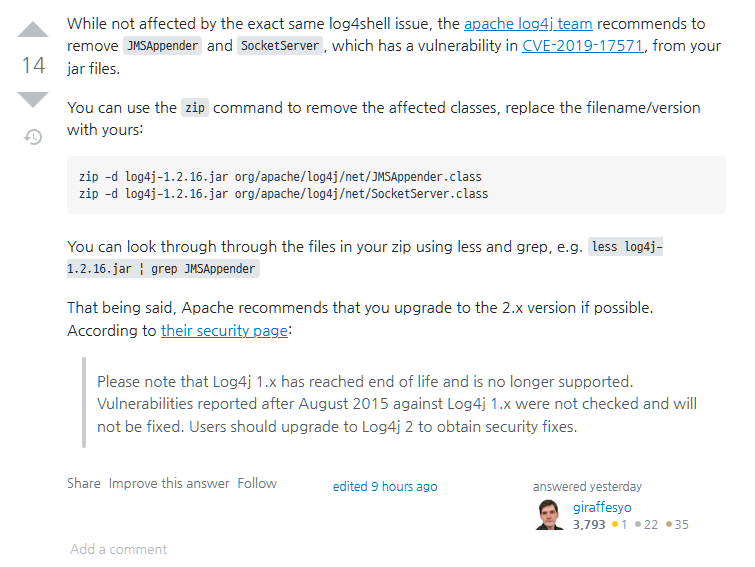
While not affected by the exact same log4shell issue, the apache log4j team recommends to remove JMSAppender and SocketServer, which has a vulnerability in CVE-2019-17571, from your jar files.
You can use the zip command to remove the affected classes, replace the filename/version with yours:
zip -d log4j-1.2.16.jar org/apache/log4j/net/JMSAppender.class zip -d log4j-1.2.16.jar org/apache/log4j/net/SocketServer.classYou can look through through the files in your zip using less and grep,
e.g. less log4j-1.2.16.jar | grep JMSAppenderThat being said, Apache recommends that you upgrade to the 2.x version if possible. According to their security page:
Please note that Log4j 1.x has reached end of life and is no longer supported. Vulnerabilities reported after August 2015 against Log4j 1.x were not checked and will not be fixed. Users should upgrade to Log4j 2 to obtain security fixes.
log4j-vulnerability - Is log4j1.2.17 vulnerable (was unable to find any jndi code in source)?
With regard to the log4j jndi remote code execution vulnerability that has been identified CVE-2021-44228 - (also see references) - wondered if Log4j-v1.2 is also impacted but the closest I got from
stackoverflow.com
#log4j-vulnerability
'WorkHolic' 카테고리의 다른 글
| Log4shell 첫 발생 외 (0) | 2021.12.16 |
|---|---|
| Apache Log4j 1.2.x 버전 취약점 해결 방법 #2 (0) | 2021.12.16 |
| SELinux 설정 (0) | 2021.12.10 |
| MySQL Proxy (0) | 2021.11.10 |
| 403 4.7.0 TLS handshake failed (Sendmail) 해결하기 (0) | 2021.10.13 |

